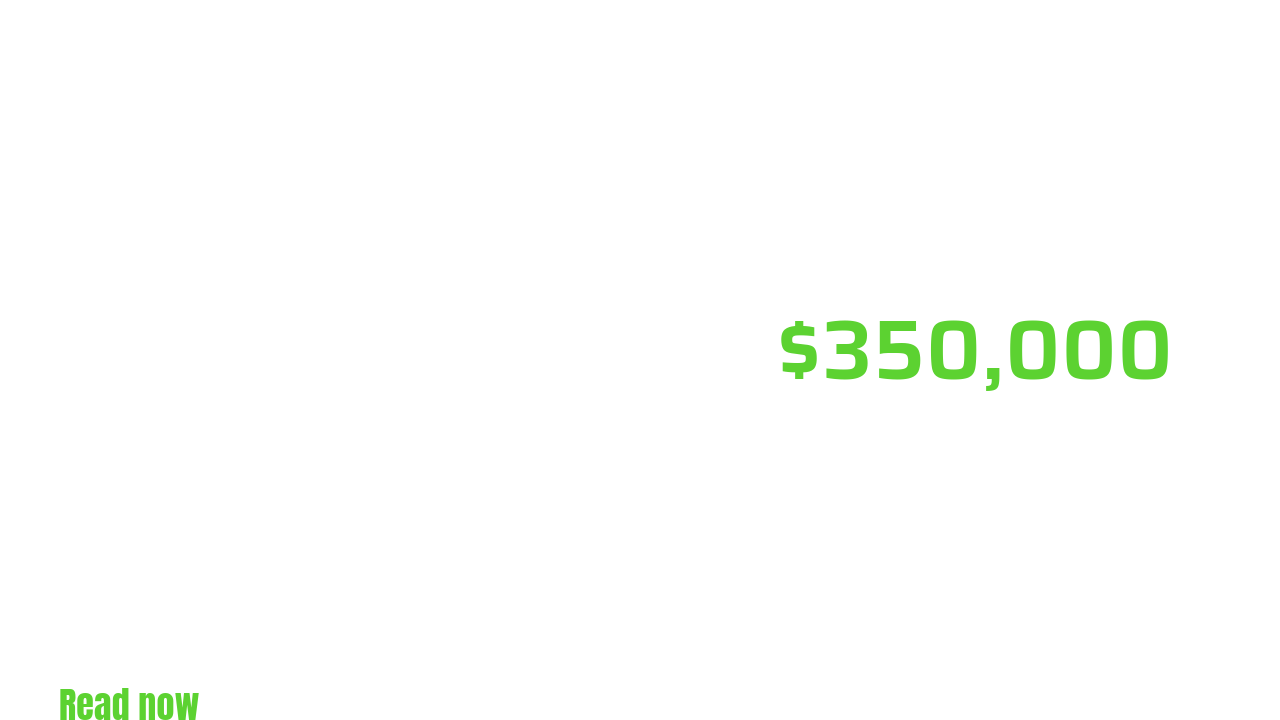In the rapidly evolving world of cybersecurity, cloud security breaches have become a major concern for businesses across all sectors. According to the latest CrowdStrike Global Threat Report, cloud intrusions...
At SafeNet, we continuously monitor the evolving landscape of cybersecurity threats to ensure our clients are protected against the latest vulnerabilities. Recently, a critical remote code execution (RCE) vulnerability has...
AT&T recently made a controversial decision, paying hackers upwards of $350,000 to delete customer data stolen in a major breach last week. While some may see this as a quick...
The cybersecurity landscape is ever-evolving, with new threats emerging at a rapid pace. To stay ahead, continuous learning and skill enhancement are crucial. OffSec, a leader in cybersecurity education, has...
In recent times, Microsoft has issued recalls for certain versions of its Windows operating system due to critical vulnerabilities and other significant issues. These recalls are not just technical nuisances;...
As the clock ticks down to October 14, 2025, many businesses and individuals are preparing for the end of Windows 10 support. This pivotal moment marks the cessation of security...
In the ever-evolving landscape of cybersecurity, the Offensive Security Certified Professional (OSCP) certification has emerged as a gold standard for aspiring ethical hackers and penetration testers. Known for its rigorous...
In the rapidly evolving field of cybersecurity, staying ahead of threats requires continuous learning and skill development. Offensive Security (Offsec) training has emerged as a cornerstone for cybersecurity professionals seeking...
In the realm of cybersecurity, firewalls play a crucial role as the first line of defense against external threats. However, their functionality goes beyond merely blocking unauthorized access. Firewall logs,...
In today’s digital age, virtual events have become an integral part of business operations, education, and social interactions. From webinars and online conferences to virtual trade shows and remote team...